Risk Summary
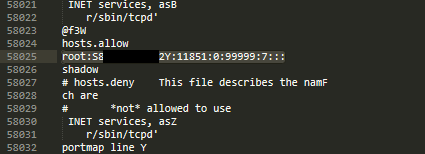
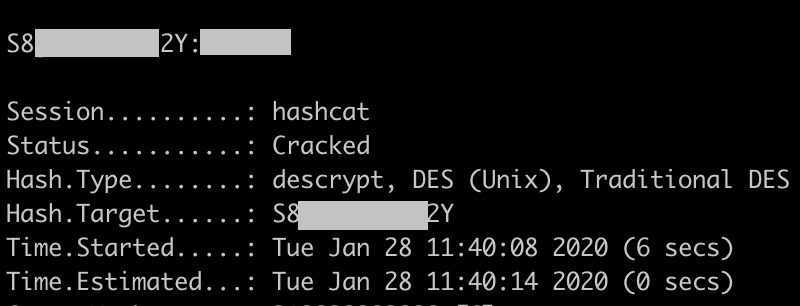
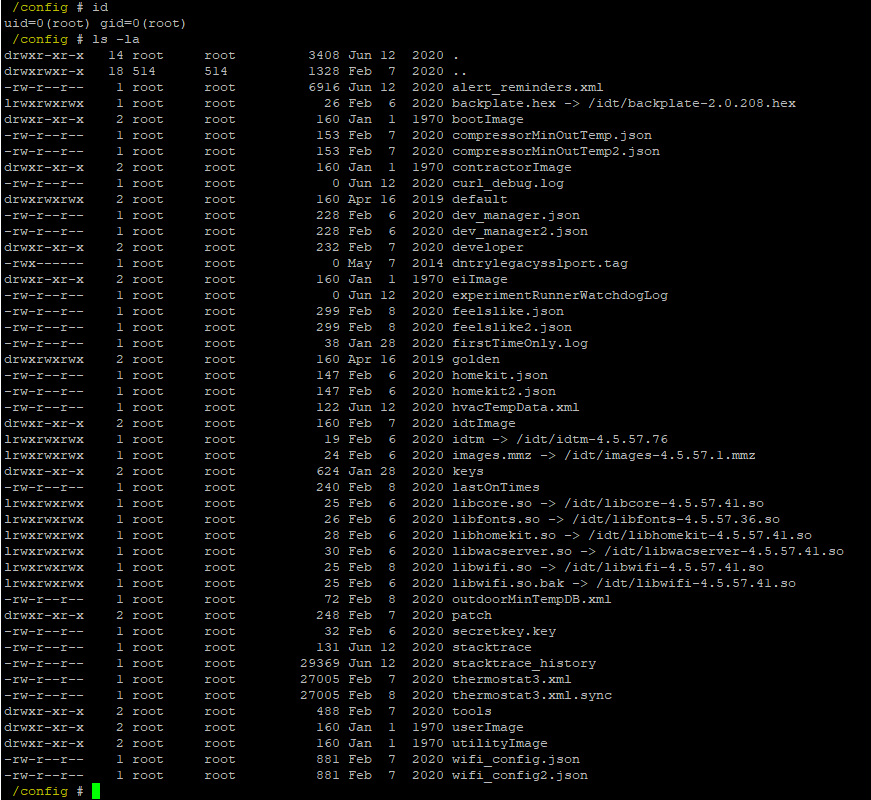
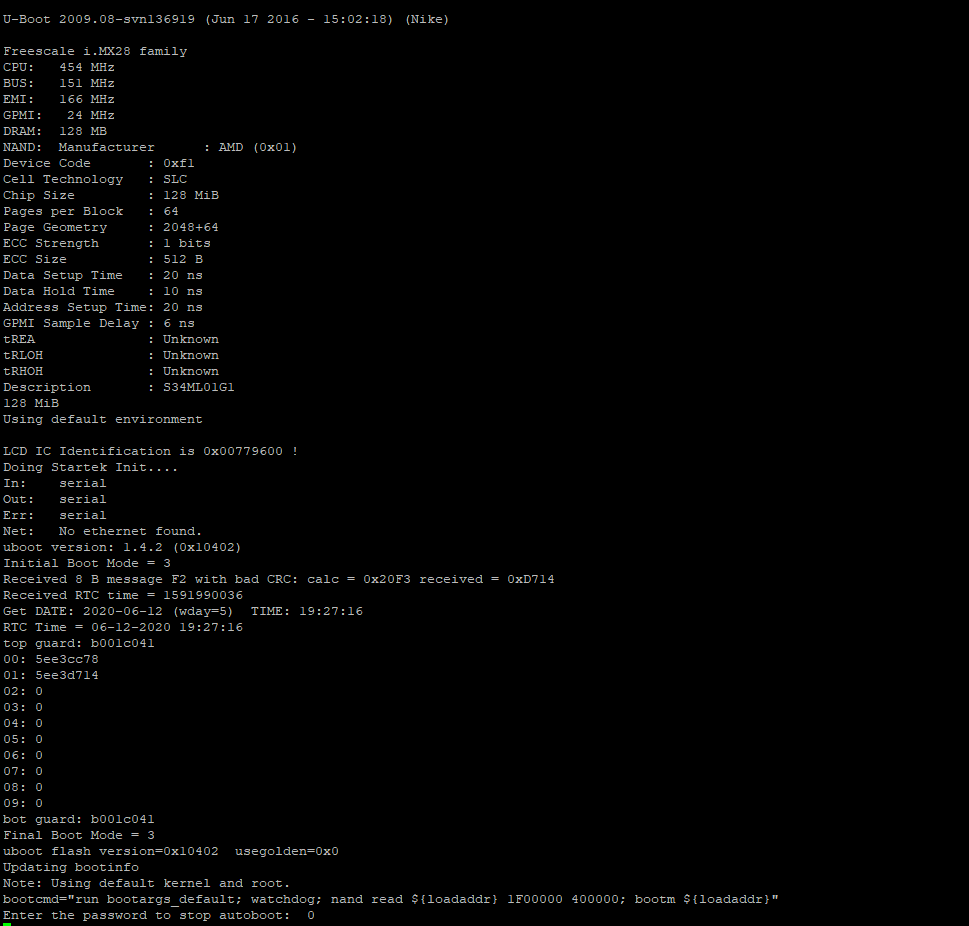
Hard-coded default root credentials exist across all devices, potentially allowing a threat actor to gain privileged access to the ecobee3 lite device. The root passwords reserved for admin users can be discovered through analysis of the compiled firmware via reverse engineering. The password is stored in a hash format but lacks complexity and can be easily brute-forced. Using the cracked password a threat actor can gain access to the serial console on the device. The threat actor could use this privilege to extract sensitive information or modify the device.